In the previous post, I created the microservice and got it’s output logging to both the console and a file target using NLog.
In this post I’ll be creating an AppConfiguration resource in Azure, reading a value from it in the microservice and then, acting accordingly on the value.
1. Setting up AppConfiguration in Azure
2. Integrating the AppConfiguration into Program.cs
3. Adding a conditional functionality to the logging output.
1. Setting up AppConfiguration in Azure
Open up Azure and select (for me, Free services) AppConfiguration
Create the resource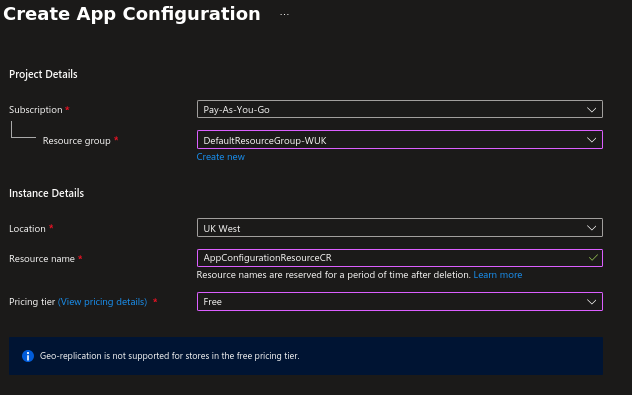
Setup the access type, I’ve gone for local in this instance, as it’s going to be a simple access.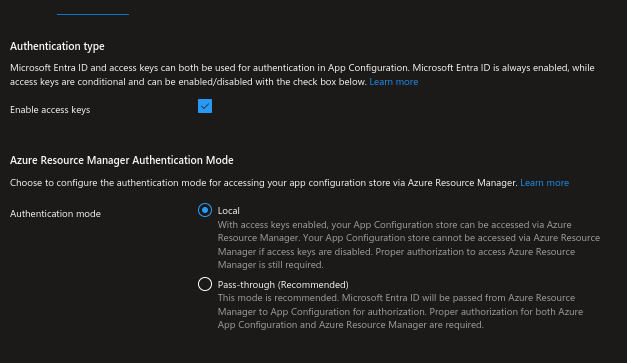
Create a key/value pair, in this instance I’ve added a simple string to determine the output of any logs.
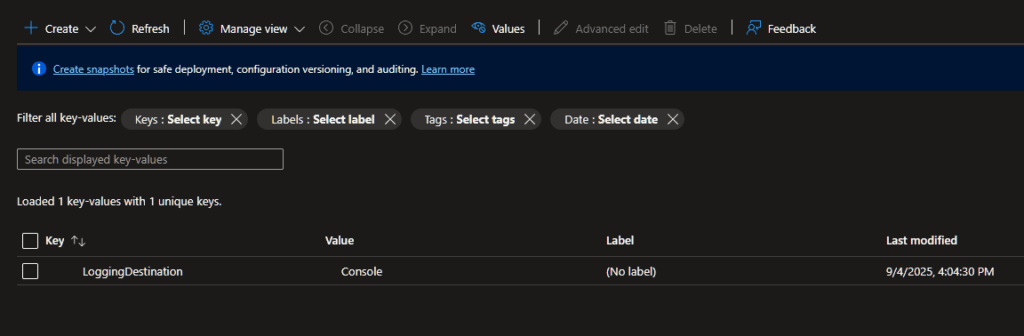
2. Integrating the AppConfiguration into Program.cs
Now that the simple AppConfig keyValue pair has been created it’s time to add the functionality into the program.cs in order to be able to read the value from azure.
using nuget in VSCode. Install the packages:
Microsoft.Extensions.Configuration.AzureAppConfiguration
Azure.Identitythen add these into program.cs
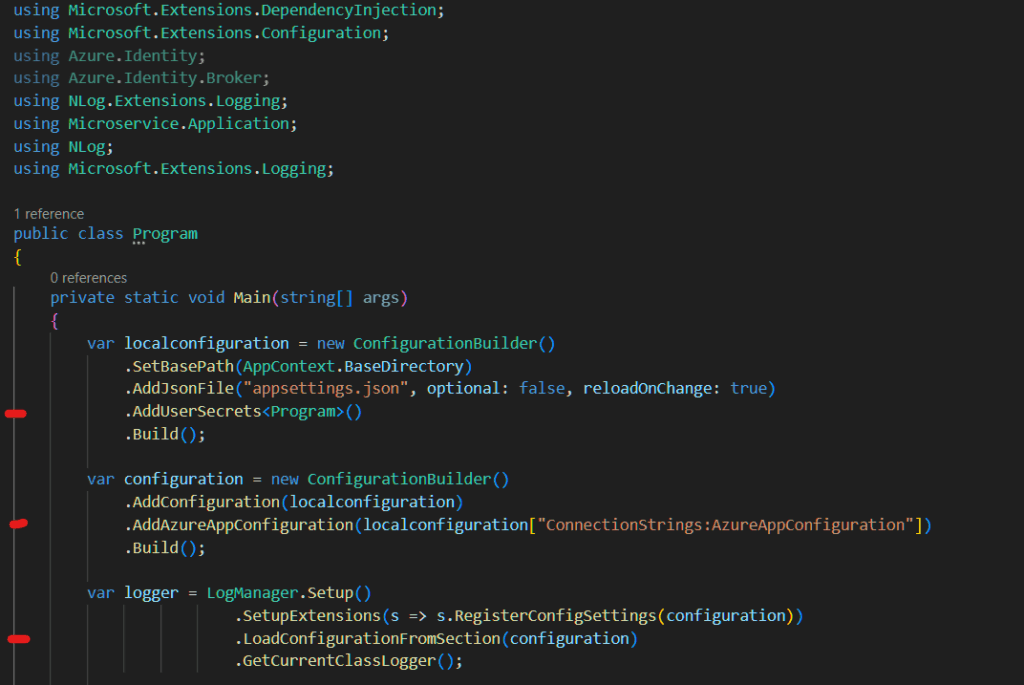
The first mark adds the usersecrets from the executing assembly (the filename is stored in the project file). This is all built to create a local configuration
The second mark adds the azure app bindings, using the local configuration as a base (the local needs to be built first in order to access the connection string)
The third mark then loads in all the configuration.
Now that this is in, you can either use a Local Environment variable, or secrets.json to store the AppConfigEndpoint. When I first did this, I ended up using an Environment Variable, but have since switched to using secrets.json because it’s less fiddly.
following the instructions from this safe storage of app secrets on the Microsoft documentation website, I created the connection string using the following powershell commands:
dotnet user-secrets init
dotnet user-secrets set "ConnectionStrings:AzureAppConfiguration" "<My Endpoint>"
When I first did this I thought, “why can’t I just use the appsettings.json“? But obviously, this would require storing an endpoint and secret into the appsettings.json, which isn’t secure. Now secrets.json is only local to the current logged in user. So our secrets are nice and safe. When deployed, they won’t be included with the app, as it will already be reading from the Azure App Configuration.
Azure App Configuration values can then be accessed in code like:
var myConfigValue = config["LoggingDestination"]3. Adding a conditional functionality to the logging output.
Now that we’ve added in the Azure App Configuration, update the MyApplication.cs and read the value from it.
_configuration["LoggingDestination"] == "Console"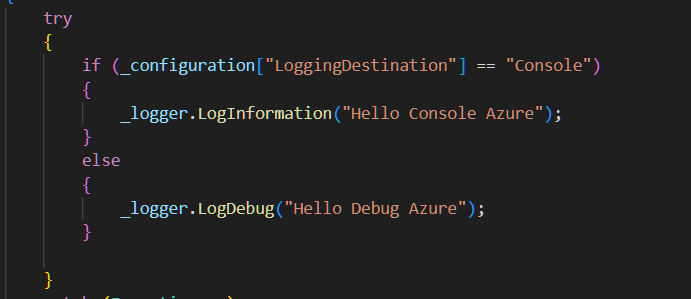
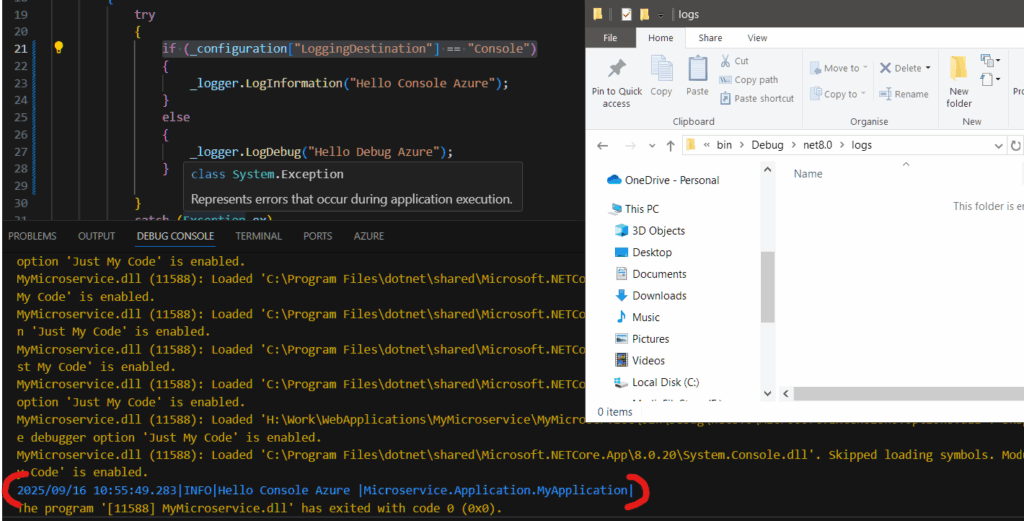
using the “console” value in Azure (output to the console, nothing in the logs directory)
using a “Debug” value in azure (no output to console, file created in logs directory)
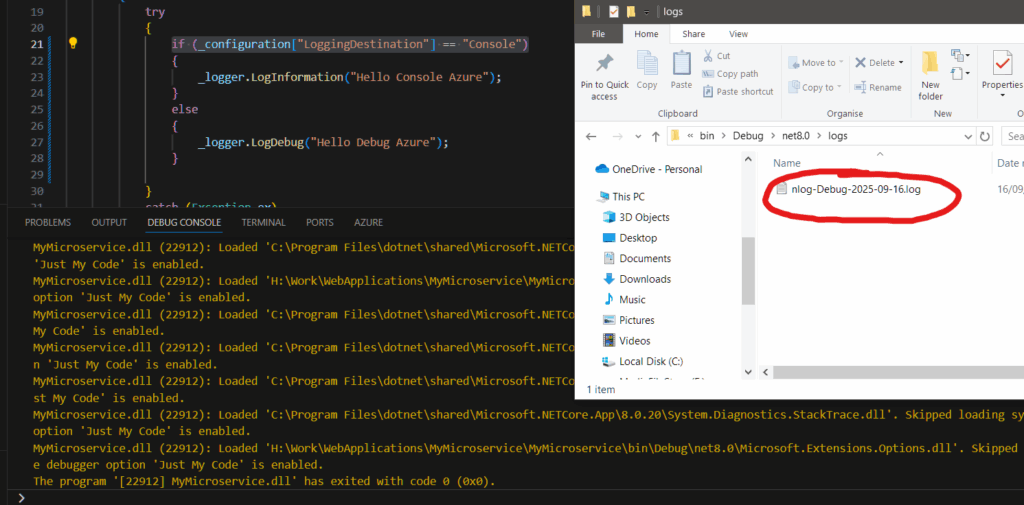
And there we have it, a conditional based on a value set within Azure AppConfiguration. This can be changed on the fly without having to restart, or rebuild the application.
This can also be utilised to read values from Azure KeyVault, which I’ll go through in the next post.